I followed the instructions as I’m getting familiar with using Git and Github for this project. I moved the keystore file away from the project, to store it somewhere else that wouldn’t end up being tracked in git and visible on github.
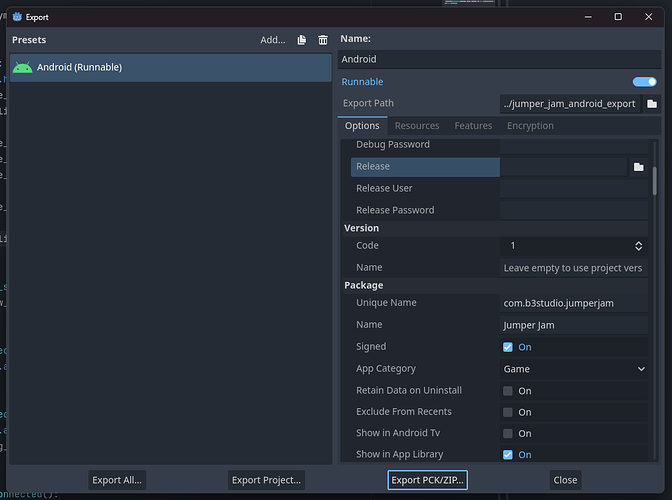
Unfortunately, there is something else to do that isn’t mentionned here. When exporting your build, make sure to not save before you actually erase the infos contained in:
Release
Release User
Release Password
If you save, commit and push, everything you have here will end up online and clearly visible, your password will be exposed.
I guess adding the “export_credentials” file that can be found in the .godot folder would have prevented this… unfortunately I clearly didn’t see that one coming as I’m too inexperienced. I had to switch my repo to private and right now I’m not sure how to get rid of the leaked infos.